How to raise a tech genius

Teach computing with everyday household objects
Teaching your children core computing concepts at home needn’t be a nightmare. In this article, Shahneila Saeed and her fantastic colleagues at Digital Schoolhouse show you how you can use everyday objects found in your house to carry out fun activities with your child and teach computing concepts without computers.
These fun fifteen-minute activities assume no prior knowledge or understanding of computing and enables parents to learn skills and concepts alongside their children. They are quick, easy and have been developed using first-hand teaching expertise, in addition to being fully mapped to the computing curriculum taught in schools.
You can follow along with the videos below, courtesy of Digital Schoolhouse, or follow the step-by-step instructions in this article.
Enjoy!
Activity 1: BINARY PLAYING CARDS
Find out how to represent binary numbers using playing cards
What you need:
- Playing cards
Recommended age range:
Suitable for all ages
What to do
Take the following playing cards, from any suit, from a standard deck of cards: an Ace, two, four and eight.
In this example the Ace will be equal to one.
Lay out the cards face up on the placeholder worksheet:

Where the card is face up it represents a 1 in the binary number and you should include the number on the card when adding the place values together. A face-down card represents a 0 in the binary number.
These cards represent the following binary number: 1111. The decimal number they represent is 15 (8 + 4 + 2 + 1 = 15).
The binary number represented here is 1100 and the decimal number 12 (8 + 4 = 12).
Now try the combinations below. Can you work out what decimal number each binary string represents?
| Binary
|
Decimal
|
| 0000 | |
| 0001 | |
| 0010 | |
| 0011 | |
| 0100 | |
| 0101 | |
| 0110 | |
| 0111 | |
| 1000 | |
| 1001 | |
| 1010 | |
| 1011 | |
| 1100 | |
| 1101 | |
| 1110 | |
| 1111 |
What you’re learning
The activity explains how binary place value works. Just like in decimal, the place value of the number on the far right is always 1. Unlike decimal, each new additional place value added to the left of this number is double the previous place value: 1 then 2, then 4 and then 8, but in this order: 8421.
A 1 or 0 is then used to represent whether to include that place value in the total or not.
1111 means add all the place values together to equal 15.
1010 means add 8 and 2 to equal 10.
Activity 2: HAMA BEAD ASCII
Represent your name in Hama beads using binary and ASCII code
What you need:
- Hama beads
- Hama bead pegboard template with a width of at least seven pegs
- Iron
- Baking paper
- Paper
- Pen
Recommended age range:
Suitable for all ages (care will need to be taken with ironing the Hama beads if working with younger children)
What to do
Write out your name leaving space after each letter. To keep things simple let’s use capital letters only. For example:
D
I
G
I
T
A
L
Look up the binary value of each of your letters:
| Decimal
|
Binary
|
ASCII Character
|
| 65 | 01000001 | A |
| 66 | 01000010 | B |
| 67 | 01000011 | C |
| 68 | 01000100 | D |
| 69 | 01000101 | E |
| 70 | 01000110 | F |
| 71 | 01000111 | G |
| 72 | 01001000 | H |
| 73 | 01001001 | I |
| 74 | 01001010 | J |
| 75 | 01001011 | K |
| 76 | 01001100 | L |
| 77 | 01001101 | M |
| 78 | 01001110 | N |
| 79 | 01001111 | O |
| 80 | 01010000 | P |
| 81 | 01010001 | Q |
| 82 | 01010010 | R |
| 83 | 01010011 | S |
| 84 | 01010100 | T |
| 85 | 01010101 | U |
| 86 | 01010110 | V |
| 87 | 01010111 | W |
| 88 | 01011000 | X |
| 89 | 01011001 | Y |
| 90 | 01011010 | Z |
For example:
| D | 01000100 |
| I | 01001001 |
| G | 01000111 |
| I | 01001001 |
| T | 01010100 |
| A | 01000001 |
| L | 01001100 |
Now choose two colours of Hama bead, one to represent 1s and one for 0s.
I am going to use white to represent 1s and black for 0s.
Place the Hama beads onto your pegboard according to the binary number for each letter.
Here I have laid out the Hama beads to represent the binary number 01000100 which represents the letter D in ASCII: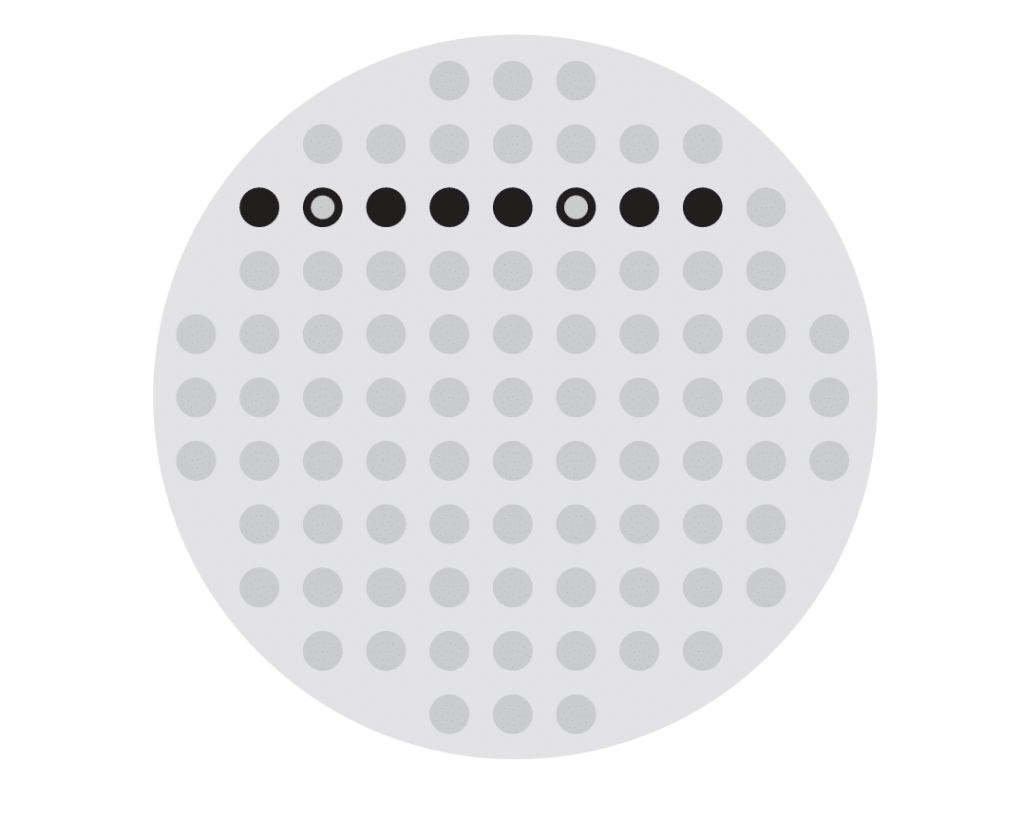
Add the rest of the Hama beads needed to represent your name: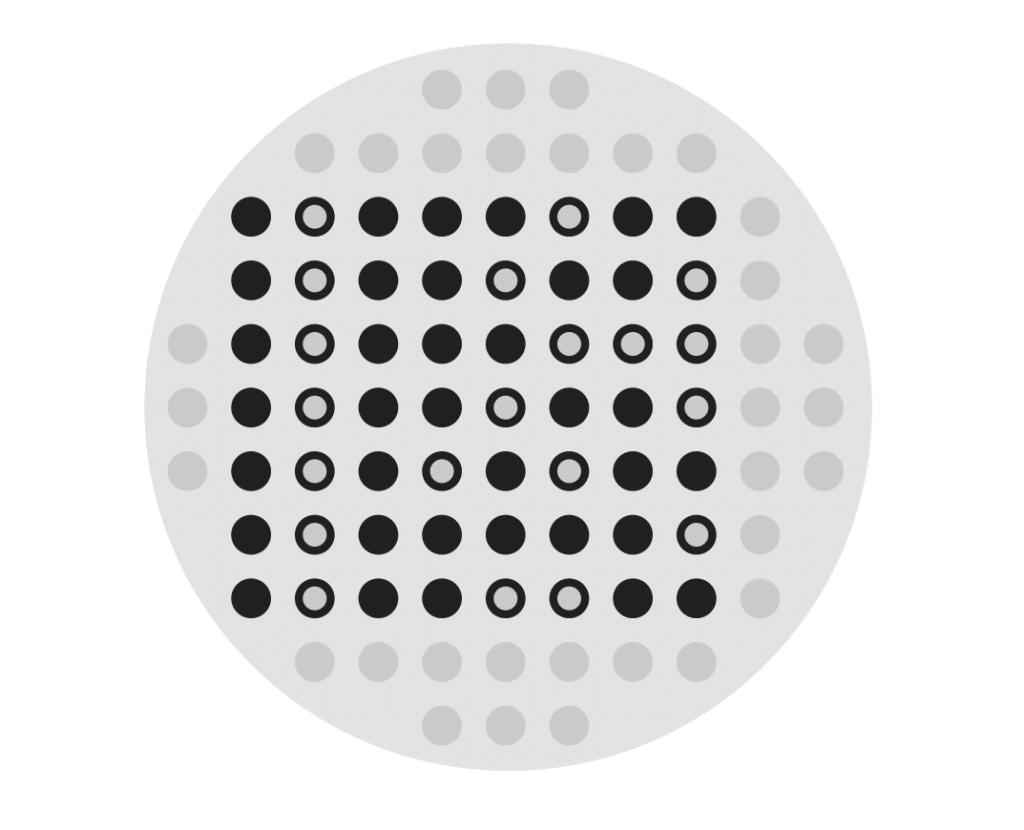
Fill in the rest of the space on your pegboard with a third colour: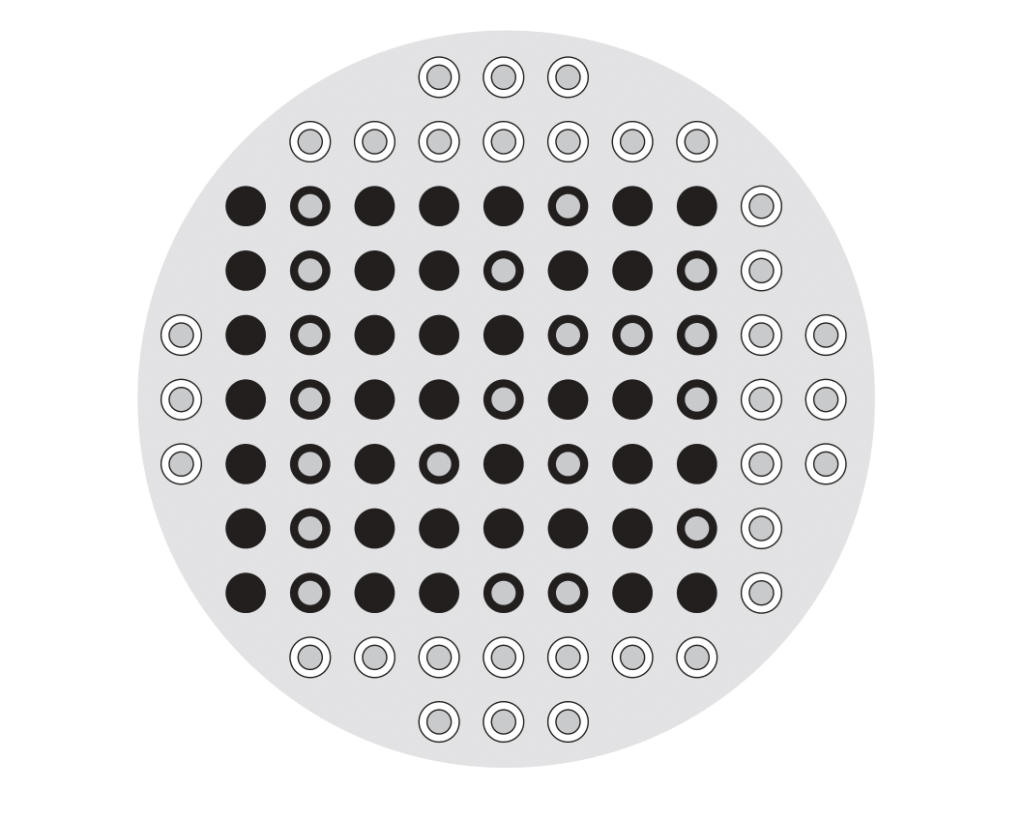
Cover your completed pegboard with the baking paper and then iron to melt the Hama beads together.
You have created a coaster with your name in ASCII and binary.
What you’re learning
Everything on a computer is represented using binary, including letters. In computer science we call everything that you can type on a keyboard a character; this includes letters, numbers, symbols and control keys like enter and tab.
In the early sixties the American Standard Code for Information Interchange (ASCII) was developed in order to provide a standard character set for computers and electronic devices. Until then different companies used different character sets in their devices and so computers from different manufacturers were unable to communicate with each other as the binary number 01000100 might be a D on one computer but A on another.
ASCII uses 7 bits to represent 128 characters with an 8th bit being used as a check to make sure the binary number is correct (this is always a 0).
Activity 3: CACHE IN HAND
Learn about storing instructions in the cache, in the computer’s CPU
What you need:
- A4 picture (for example, of a celebrity)
- Pencil
- Ruler
- Scissors
- Stopwatch
- Tray
Recommended age range:
Suitable for KS2, KS3 and KS4
What to do
Find a large picture from somewhere in your house. You could print it or look in a magazine or newspaper. Can you find your favourite? You might find that using the front page of a magazine or printing your image onto card makes solving the puzzle a little easier.
You will be dividing the picture into thirty-two pieces (eight horizontally and four vertically). Use a pencil and ruler to draw horizontal lines across the picture. Can you space them equally? Now do the same with vertical lines. Have you got thirty-two pieces? Now cut them out. Take the first two rows of pieces of your image (eight pieces) and put them to one side. Mix up the rest of the pieces.
Place a tray on a table or on the floor at one end of your room. Place the eight pieces you set aside close to the tray and put the other twenty-four pieces at the other end of the room.
How quickly can you solve your jigsaw puzzle and put the picture back together again? Start the stopwatch and make your picture. You could work with another person to create a competition to see who can solve it fastest!
What you’re learning
The computer’s brain is the CPU. It contains registers and caches to store instructions. In our activity, the register held the first eight pieces close to the tray. Your most commonly used instructions get stored here for easy access. To illustrate this we put the first eight pieces of the picture aside to make solving the puzzle quicker. The cache is another place to store instructions. The cache can contain more instructions, but it takes longer to fetch them. That is why you needed to run to the other end of the room to collect the pieces of the picture.
INPUT –> PROCESS –> OUTPUT
You input the data (the pieces of jigsaw), process the data (decide where to put the piece to make the picture) and the output is the final jigsaw picture.
Activity 4: PACKET SNIFFING
Learn about packet switching by sniffing out chocolate hidden in envelopes.
What you need:
- Three different types of small chocolate bars
- Twelve envelopes, each big enough to take two pieces of chocolate
Recommended age range:
Suitable for all ages
What to do
- Let your child sniff each chocolate bar to get an idea of what they smell like. Once they have done this break the bars into pieces and share the pieces of each bar between four envelopes (do not mix the chocolate bars up, you should have four envelopes of each type of chocolate).
- Repeat this so that you have twelve envelopes all with chocolate in them.
- Seal the envelopes so the chocolate won’t come out and can’t be seen. Mix the envelopes up.
- Let your child smell each envelope, one at a time, and sort them into three separate piles. One pile for each type of chocolate. Can they name them?
- Once they have done this open the envelopes up. If they have managed to get four envelopes in the same pile with exactly the same chocolate in them, they get to eat the chocolate. If they have managed more than one, they should obviously share with you! If they haven’t managed to do any, then let them have another go until they get it right.
- Ask them to think about furniture when it is delivered. Packages come in all sorts of different shapes and sizes. It is the same with data on computers – sometimes we get text, other times images or videos. Most are too large to send all in one packet, so we break them up into smaller packets. Imagine if we sent them over the internet with no labels to say what they are? What do you think would happen?
Now try this
- Repeat step 1 above. You may want to start again with fresh chocolate bars or put the originals – if they haven’t been eaten – back in the envelopes.
- Now get some other family members involved and spread out across the room.
- Designate one family member at the other end of the room to receive the chocolate. Can they open the envelopes for only one type of chocolate? So, for example, if you had a Twix bar, Cadbury’s Whole Nut and a bar of Galaxy Chocolate, can they open up only the envelopes with the Twix pieces in them?
- Mix it up:
- Family member 1 wants a Twix
- Family member 2 wants the bar of Whole Nut
- Family member 3 wants the bar of Galaxy
- How can you make sure that each family member gets only the envelopes containing the chocolate that they need? Additional information is required. But what information is this? Allow plenty of opportunity for discussion and try out as many different scenarios as you can, even if they don’t look like they’ll work. Your child will learn from the trial-and-error element.
- Essentially, you’d need the following items of information written as labels on the envelopes:
- Name of chocolate
- Who the recipient is
- The packet number
- Total number of packets to expect
What you’re learning
When computers send packets of information over networks (i.e. the Internet), each packet has the following information sent with it:
- Recipient address, normally an IP address (a unique identifier for an internet-enabled device)
- Title of the file
- How many packets of information make up the file
- What part of the file the packet is so it can be put back into the right order. For example it might be the eleventh packet of forty-five
It will then have the actual part of the file that is being sent. These packets make their own way through the internet to their destination and then the device at the receiving end will put the packets back together to form the whole file.
What is packet sniffing? And how is this related to security?
Packet sniffing is the act of capturing a data packet that is being sent across a computer network. It is similar to what you might see in the movies when they ‘wiretap’ a telephone line (network). Packet sniffing is mostly used by hackers who are illegally collecting information about the network.
Internet Service Providers (ISPs) use packet sniffing to track all your activities such as:
- Who are you sending your email to?
- What is inside the email?
- What are you downloading?
- What websites do you visit?
- What do you look for on that website?
- Did you download anything from that website?
Do you stream video? If so, what?
Digital Schoolhouse
Digital Schoolhouse, together with Nintendo UK, uses play-based learning to engage the next generation of pupils and teachers with the Computing curriculum. Digital Schoolhouse is delivered by the UK games industry trade body Ukie and is supported by the Department of Digital, Culture, Media and Sport (DCMS). Our ingenious computing workshops are aimed at local primary schools across the UK. Delivered by our expert network of Schoolhouses and lead teachers, you can experience our unique approach to play-based learning through innovative activities and free adaptable resources. Underpinned by evidence-based research and combined with groundbreaking careers education, the programme successfully bridges the gap between academia and industry, to ensure pupils are aptly equipped for the future digital economy.

Teach computing concepts without computers! How to Raise a Tech Genius makes the computing curriculum accessible for parents and families.
We live in a digital world - one in which our children are surrounded by technology. It's a part of their lives in a way that even the most tech-savvy adults aren't fully able to comprehend. What we do know is that the workplace of tomorrow will require our children to harness the power behind the technology, to be able to understand key concepts and apply them. Logical reasoning, creativity and problem solving are skills that are becoming increasingly essential in the world of work.
How can we best prepare our children to enter this world? How to Raise a Tech Genius is a practical book that assumes no prior knowledge or understanding of computing and enables parents to learn skills and concepts alongside their children. The quick, easy and fun fifteen-minute activities within the book have been developed using first-hand teaching expertise and are fully mapped to the computing curriculum taught in schools.
From a deck of playing cards to the story books on your bookshelf or even the contents of your fridge, How to Raise a Tech Genius uses everyday objects that can be found around your home to illustrate core computer science concepts. Children and adults alike will enjoying playing games while developing their algorithmic thinking and logical reasoning skills. This book demystifies the computing curriculum for adults, showing parents a whole new side of computing, coding and technology so that they can help their child become a computing genius!








